Private banks worldwide are being approached by wealthy individuals who say they became rich by investing in cryptocurrencies. These individuals want their cryptocurrency assets be managed, and naturally go to private banks for that.
So my view’s quite clear. I believe cryptocurrencies, Bitcoin is the first example, I believe they’re going to change the world.
by Richard Brown
These banks and wealth managers would welcome a tool that can give them a confidence level in the "cleanliness" of funds submitted to them. This tool should also let the customers cherry pick the assets they want to manage. In a nutshell, the tool has to analyze the transaction history of each asset in each wallet/portfolio and compare it against all known Money Laundering schemes, and then issue a report on the risks of handling this kind of resources.
Our algorithms will enable Real Time API and incrementally calculate the risk rates. One of cornerstone idea is to use transaction data and standard behaviour, then econophysics and stochastic models to group accounts to user.
We are pioneers in cryptocurrency intelligence and AML policy implementation.
At this moment in time, blockchain and information revolution have reached its mature phase that enable us to do what was previously dreamed about. Therefore, we must use this chance and set the standards for others to follow.
Financial institutions must implement AML measures, yet they see it as big expenditures and a loss of time. It is thus an opportunity on which we capitalize, offering services to their compliance department to alleviate the hard work of uncovering suspicious trails the assets have traveled.
Risk Index
Address Classification: for the time, we have opted for seven types of cryptocurrency owner groups, and a coloring scheme to foster an intuitive reading of our reports. The information about which owner belongs to which type is gathered by our algorithms as well as in cooperation with state and private agencies who will provide us trustable data of criminal addresses. For some of these types, we can formally declare that they are illegal.
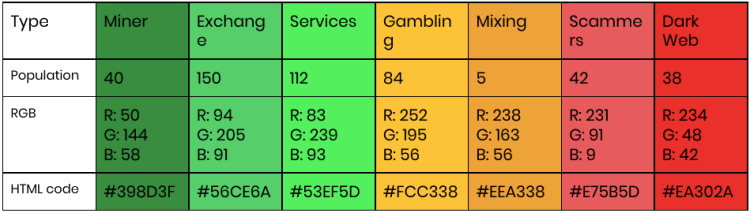
Our report will show all the data and the risks of accepting this asset. The customer makes the final choice. We’ll use multiple sources of info and we’ll categorize our results in three cases:
First case: for which we give red flag and guarantee that it’s
illegal coins with 100%
Second case: we’ll assign probability of that it’s illegal coins
from 1% to 99%
Third case: is coins for which we can guarantee that are totally
legal, i.e. the risk rate is 0% for the customer to handle this asset.
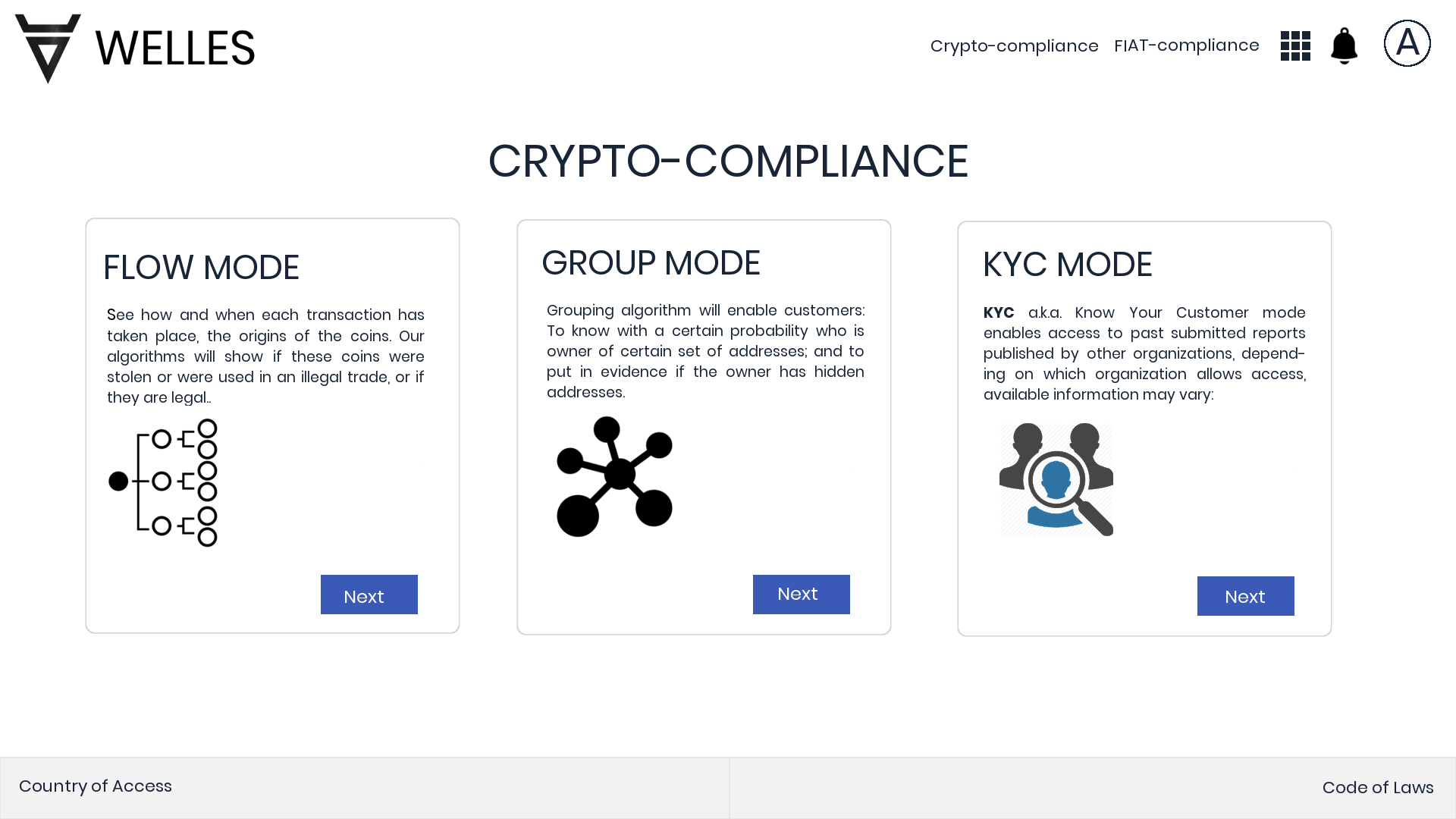
Crypto-Compliance Service Modes:
Our database consists of many types of suspicious activities and schemes, known to have happened before on blockchains, known cases of schemes and frauds published by FinCEN. We combine this data with tagging alert flags, to signal possible money laundering activities.
Flow Mode
Our services do real time monitoring of suspicious activities. Fast and quick actions are needed and customers will be informed the very moment the activity is taking place.
We choose one Target Address and analyze its transaction flows through history.
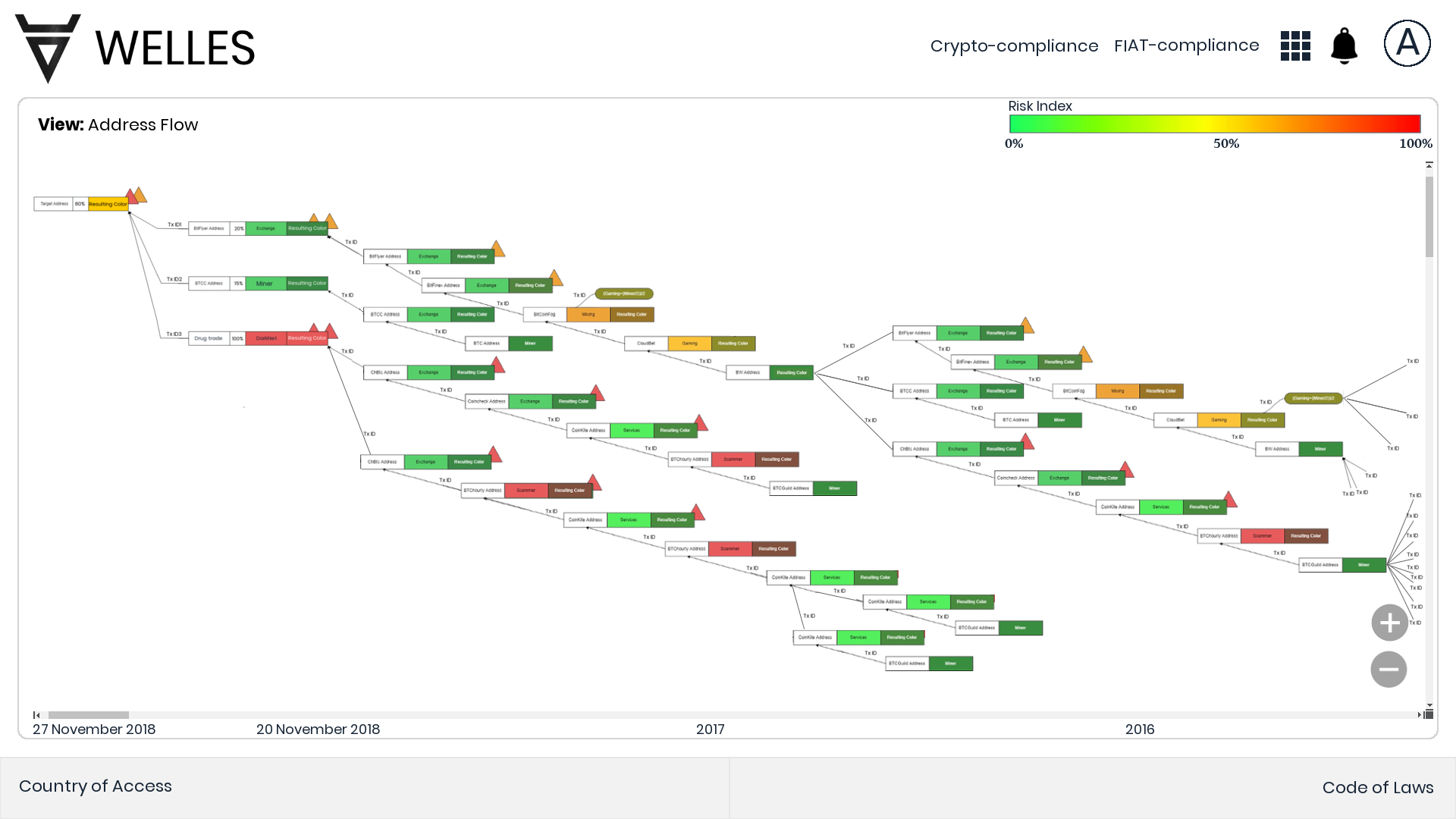
For more details look the demo video.
Grouping Mode
Grouping algorithm will enable customers: To know with certain probability with whom is owner of certain set of addresses; and to check if the owner has hidden addresses.
For more details look the demo video.
KYC Mode
KYC a.k.a Know Your Customer mode is shared database of already checked customers between different entities with a filter on level of access.
For more details look the demo video.
Sum up
When John Smith comes in a bank and says that he owns 100 BTC on address #12345.
The bank official is supposed to know:
1) Where the coins come from on address #12345; the legality of them as well as
the total money flow history through which coins went from moment of mining or
STO issuance.
2) The bank official will also know all the other addresses that John Smith owns
(with probability), their balances as well as the legality of the assets on
these addresses.
CRYPTO-COMPLIANCE data sources:
■ Proprietary Welles discovery
algorithms and analysts
■ Public sources
■ Honeypots and other active
capture sources
■ Trusted communities,
including law enforcement and regulators
■ Welles Crypto Recovery
Network
■ APWG eCrime Exchange
(eCX)






